Why using Datasafe
Security of data is a major issue that needs to be addressed because companies must comply with an increasing number of laws, standards, and codes of conduct relating to information security: General Data Protection Regulation (GDPR): If a company wants to achieve GDPR conformity, it must take data protection measures. Companies that have critical infrastructures must also catch up IT security according to the IT security law, for this they must also guarantee data security. The loss of sensitive data during hacker attacks, for example, can lead to severe penalties of up to four percent of the worldwide annual turnover and can have severe consequences for a company, possibly crippling the entire organization.
Solving security issues with Datasafe
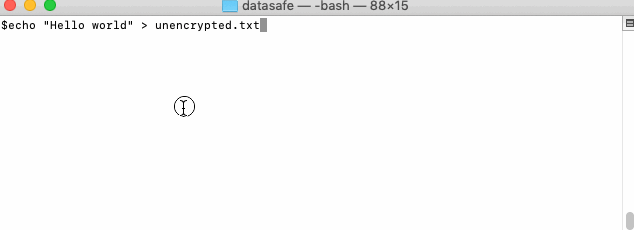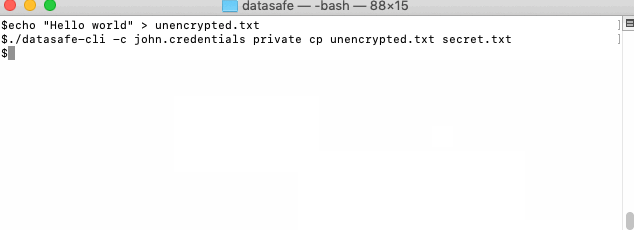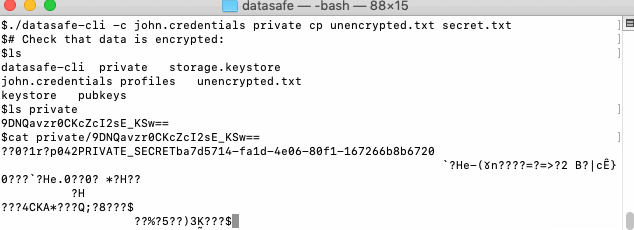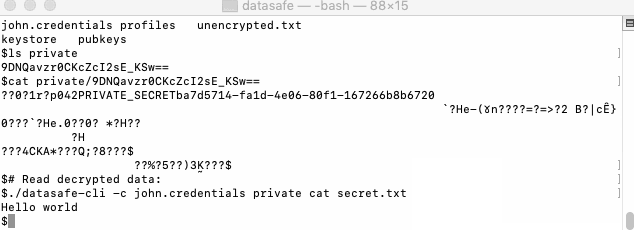
Datasafe is a cross-platform library that allows sharing and storing data and documents securely. It encrypts your data using AES-GCM algorithm and uses CMS-envelopes as encrypted content wrapper. CMS-envelope wraps and encrypts document encryption key using key encryption key that provides additional level of security. For user private files, Datasafe uses CMS-envelope with symmetric encryption of data encryption key. For files that are shared with other users (sent to their INBOX folder), Datasafe uses asymmetric encryption for data encryption key, so only recipient (or multiple recipients) can read it.
Features
- Proprietary software friendly license
- Flexibility - you can easily change encryption and configure or customize other aspects of library
- AES encryption using CMS-envelopes for increased security and interoperability with other languages
- Secure file sharing with other users
- Extra protection layer - encryption using securely generated keys that are completely unrelated to your password
- Client side encryption - you own your data
- Works with filesystem and Amazon S3 compatible storage - S3, minio, CEPH, etc.
- File names are encrypted
- Thorough testing
Quick demo
Datasafe-CLI
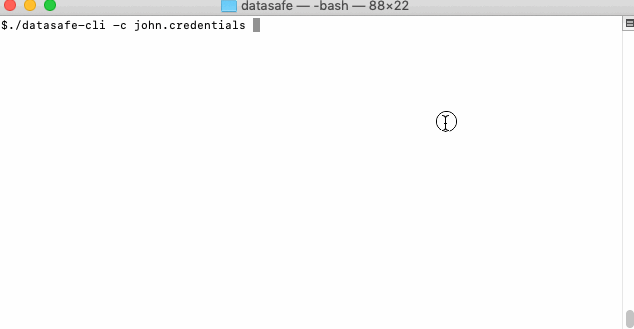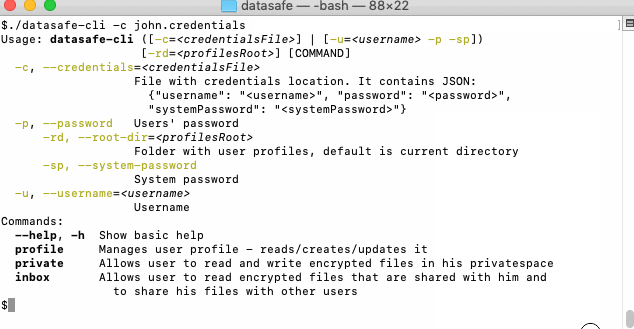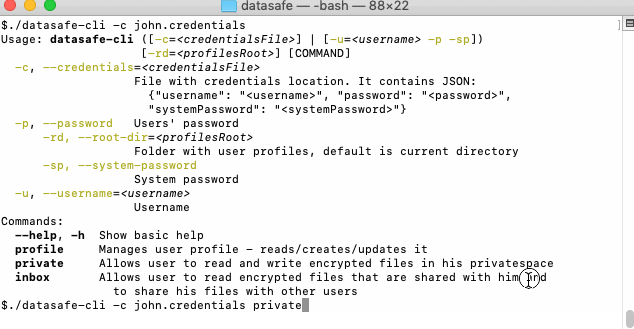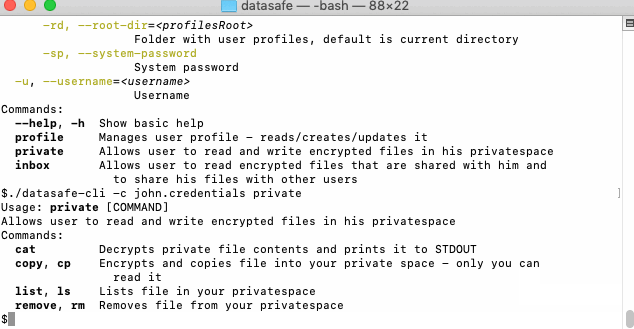
You can try Datasafe as a CLI (command-line-interface) executable for encryption of your own sensitive files. They can be saved either in S3 bucket or local filesystem (they are currently built from feature/datasafe-cli-w-s3 branch).
Download CLI executable:
- MacOS native executable
- Linux native executable
- Windows executable (N/A yet), please use java version below
- Java-based jar, requires JRE (1.8+), use
java -jar datasafe-cli.jarto execute
(Files above are built from feature/datasafe-cli-w-s3 currently)
Example actions:
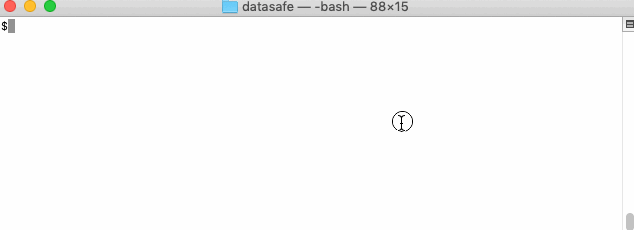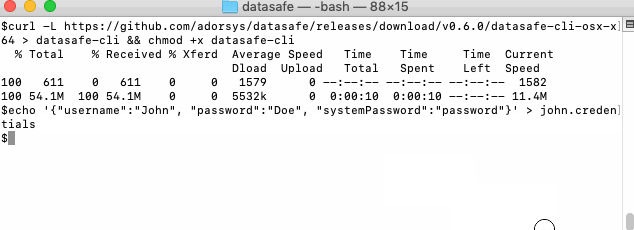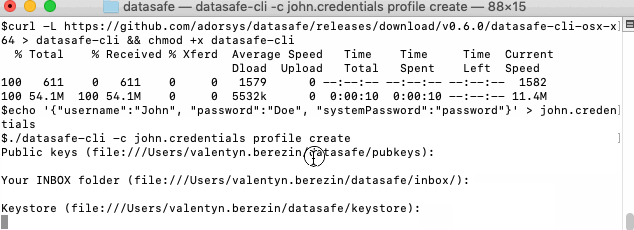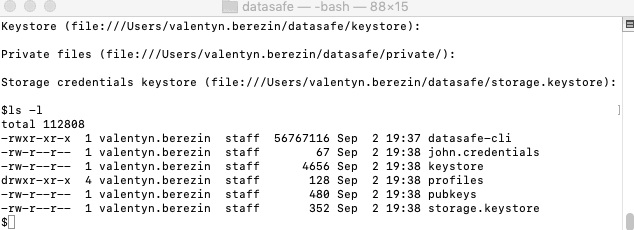
Download application and create new user:
Note: Instead of creating file with credentials you can provide credentials directly into terminal (this is less secure than having credentials file, but is fine for demo purposes):
./datasafe-cli -u=MeHappyUser -p=MyCoolPassword -sp=greatSystemPassword private cat secret.txt
Command above will show private file secret.txt content for user MeHappyUser who has password MyCoolPassword and
system password greatSystemPassword
Encrypt and decrypt some secret data for our user:
You can always list available actions in context:
REST based demo
Here you can find quick docker-based demo of project capabilities with instructions of how to use it (REST-api based to show how to deploy as encryption server).
Key definitions and functionality overview
Private space is the place where users’ private files are kept in encrypted form - something like KeePass or high-level eCryptfs for your files but built with Java in a way that you can customize anything.
Inbox is the place where shared files are stored in, they are also encrypted using users’ public key, something like encrypted file sharing, where only targeted recipients can read data that is shared with them.
Such functionality is achieved using CMS-envelopes for symmetric and asymmetric encryption. Symmetric encryption is used for private files. Asymmetric encryption is used for file sharing.
The library is built with the idea to be as configurable as possible - it uses Dagger2 for dependency injection and modular architecture to combine everything into the business layer, so the user can override any aspect he wants - i.e. to change encryption algorithm or to turn path encryption off. Each module is as independent as it is possible - to be used separately.
- Each users’ private space can reside on Amazon S3, minio, filesystem or anything else with proper adapter. In his private space, each document and its path is encrypted.
- For document sharing user has inbox space, that can be accessed from outside. Another user can write the document he wants to share into users’ inbox space using the recipients’ public key so that only inbox owner can read it.
- For storage systems that do not support file versioning natively (i.e. minio) this library provides versioning capability too.
How it works
Datasafe functionality can be viewed as virtual filesystem, that has:
- private encrypted user section - private folder, where user can list, read, write, delete his own files.
- documents that are shared with user - inbox folder, where user can list, read, delete files that were shared with him and send (write) file to some others’ person inbox.
- profile section that describes user to the system.
For example:
│
└───private
│ │
│ └─── amazon-S3
│ │ │
│ │ └───bucket1
│ │ │ │ private_file1.txt
│ │ │ │ private_file2.txt
│ │ │
│ │ └───bucket2
│ │ │ private_file1.txt
│ │
│ └───minio-in-datacenter
│ │
│ └───bucket1
│ │ private_fileA.txt
│
└───inbox
│ │ file021.txt
│ │ file022.txt
│
└───my-profile
│ │
│ └─── public
│ │ │ public.key
│ │
│ └─── private
│ | private.key
│ │ secret.key
│ │ path-encryption-secret.key
Storing private files
High-level overview of what happens when user shares his file with another user or stores something in private space:
Sharing files with another user
High-level overview of what happens when user shares his file with another user using inbox service:
Project overview
In short, Datasafe core logic provides these key services:
- Privatespace service that securely stores private files by encrypting them using users’ secret key.
- Inbox service that allows a user to share files with someone so that the only inbox owner can read files that are shared with him using private key.
- User profile service that provides user metadata, such as where is user privatespace, his keystore, etc.
These services are automatically built from modules and the only thing needed from a user is to provide storage adapter - by using predefined adapters, or by implementing his own using this interface.
Additionally, for file versioning purposes like reading only last file version, there is versioned privatespace that supports versioned and encrypted private file storage (for storage providers that do not support versioning).
Storage adapters
Out-of-the box Datasafe supports these kinds of storage systems:
- Filesystem storage. This storage uses default java.nio interface for filesystem
- S3 compatible storage. This storage uses Amazon-SDK client to get access to S3 bucket.
Additionally, user can implement his own storage adapter to support i.e. storing data inside RDBMS by implementing StorageService interface.
Project overview
JavaDoc
You can read JavaDoc here
Command to generate JavaDoc from sources:
mvn clean javadoc:aggregate -P javadoc